by Gerald McQuaid and Domenico Raffaele Cione
[vc_row] [vc_column width=”5/6″]NFV refers to the replacement of traditional specialised hardware devices with software that can be installed on standardised, off-the-shelf piece of hardware. ETSI work on NFV was initially set to address a requirement to define a list of base security requirements imposed by lawful interception in the NFV architecture.
1. NFV for 5G
The next-generation of mobile networks beyond the 4G LTE mobile networks of today is identified with the term 5G which ETSI is managing as a new technology to provide markedly increased operational performance, as well as superior user experience and better network energy efficiency (ref. http://www.etsi.org/technologies-clusters/technologies/5g). The basic performance criteria for 5G systems have been set by the International Telecommunications Union (ITU) in their IMT-2020 Recommendation (ref. http://www.itu.int/en/ITU-R/study-groups/rsg5/rwp5d/imt-2020/Pages/default.aspx). Specifically, ITU-R M.2083 [1] describes the overall usage scenarios for 5G systems in terms of Enhanced Mobile Broadband (to deal with hugely increased data volumes, overall data capacity and user density), Massive Machine-type Communications for the IoT (requiring low power consumption and low data rates for very large numbers of connected devices), Ultra-reliable and Low Latency Communications (to cater for safety-critical and mission critical applications).
The 3GPP is the mobile industry standards body most actively working on 5G standards to submit proposed specifications to the ITU to be part of the IMT-2020 standard. By the second half of 2017 the focus of 3GPP work will shift to Release 15, to deliver the first set of 5G standards – including new work as well as the maturing of the LTE-Advanced Pro specifications.
At ETSI level, most effort is on the Virtualization of the Network Function (NFV) as major key component technologies which will be integrated into future 5G systems. NFV refers to the replacement of traditional specialised hardware devices with software that can be installed on standardised, off-the-shelf piece of hardware. It’s similar to how we load various software applications on a computer. For example, instead of having a phone sitting next to your computer, you could install software that would allow you to make phone calls from the computer – and get rid of the phone on your desk. Simply put, NFV is about changing specialised communications equipment into software, and allowing the operator to bring resources to where they need them most. This should result in increased flexibility and reduced cost.
The multitude of use cases behind 5G requires the flexibility that is enabled by NFV and by extension, the open source community. NFV is now a prerequisite for having the kind of network to be able to address the IoT workload for 5G. Furthermore, the time is now for operators to formulate their strategies to transition their core network towards NFV architecture in preparation for 5G in 2020.
2. NFV Security/LI challenges
NFV greatly amplifies existing security problems in terms of impact. The vulnerabilities may be similar to todays, but it does concentrate them in one place and increase the likelihood of a common mode failure. In many ways, it puts all our “security eggs in one basket”. In traditional telecommunications equipment, a number of factors helped frustrate would be attackers e.g. physical security, proprietary software, hardware, installation and configuration, and a reduced ability to exploit any vulnerabilities. This doesn’t mean older equipment is more secure, just harder to exploit.
NFV is primarily software based i.e. all the functions of a traditional telco “switch” is now run by a virtual network function (VNF) – not unlike a program on a PC. The various functions (VNF’s) are managed by a Hypervisor. If this Hypervisor is compromised, there is little current defense to maintain integrity or confidentiality.
There are a number of sensitive functions that are of concern, significantly anything that requires encryption or isolation. Examples of these functions are authentication (key for sim card security), network defense, logging functions and above all lawful interception (LI).
Given the fact that NFV provides for a more harmonised infrastructure set, across operators and countries, any vulnerability could have much greater impact, particularly where critical national infrastructure obligations apply.
At today only a few Regulatory or Government security entities have a current understanding of the risks, more will follow.
3. LI in NFV in ETSI
ETSI work on NFV was initially set to address a requirement to define a list of base security requirements imposed by lawful interception in the NFV architecture.
The first actions were made at ETSI TC CYBER level and have resulted into two standard documents: one at recommendation level, [2] TR 103 308 v1.2.1, and another at normative level, [3] TS 103 487 v1.1.1, and both ones are usable to identify the baseline security requirements for LI as sensitive function for NFV.
At today, most standardization activity on LI in the NFV interception domain is driven by the NFV SEC sub-group within the Industrial Specification Group (ISG). NFV SEC is driving the standardization activity on LI and RD features in the NFV interception domain in coordination with TC LI.
A first phase was dedicated to identify the security and architecture pre-conditions for the provision of LI in an NVF based network. GS NFV-SEC 004 [7] was defined as a guidance on the LI requirements when deployed in the NFV context for provision of the points of interception (PoI’s) for each of Intercept Related Information (IRI) and Content of Communication (CC) with respect to the handover requirements defined by ETSI TC LI.
Particular implementation relevance was identified for the PoI location attestation and LI undetectability requirements. Latest two years most ETSI work was focused to define a feasible NFV LI Architecture starting from identifying how the standard LI Reference model (ref. Figure 2 in [5] and Figures 1 in [6]) should apply and be mapped into the new CSP architecture defined by NFV (Figure 1, see ref. [4] for NFV architecture description). Figure 1 below shows the relevant LI functional entities (drawn at left side of picture) under modelling into the new CSP NFV context (drawn at right side of picture): Administrative Function (AF), Point of Interceptions (PoI’s identified as IRI-IIF and CC-IFF) and the Internal Interfaces (INI1 also called X1, INI2 also called X2, INI3 also called X3).
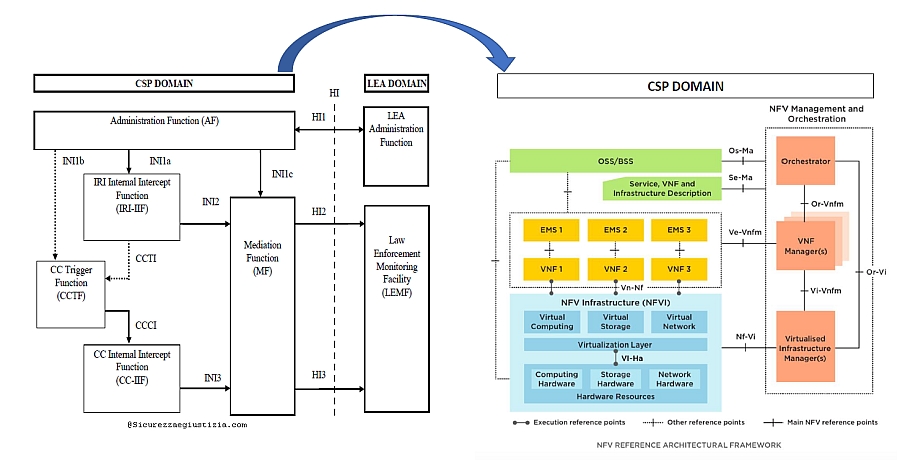
Main addressed issue was the secure configuration of the PoI when deployed as embedded or standalone VNF on top of a NFV infrastructure and how to keep it secure along the entire VNF lifecycle.
The results of this ETSI study has been formalizing into the definition of the new report GR NFV-SEC 011 [8] which represents the most advanced description of the standard solution in NFV with reference to the Lawful Interception (LI) problem Statement, Architecture, Deployment scenarios. Furthermore, mainly based on the current needs from network operators which are requested just now to manage the CSP evolution from native legacy networks towards truly virtualized networks, the report has identified the relevant most probable evolution paths identifying appropriate intermediate steps and considering a LI solution for each path as well as the associated network challenges and solutions.
Coming ETSI NFV ISG work will be focused into the definition of a new normative specification on NFV LI (GS) also starting to solve detailed stage 3 aspects for LI. These work items will represent input towards 3GPP and ETSI TC LI whose activity will be addressed to finalize the definition of the LI internal interfaces (INI1 also called X1, INI2 also called X2, INI3 also called X3), the MF/DF structuring and the HI’s possible impacts. ©
Other articles of Gerald McQuaid
 ETSI LI & RD Status (Sept. 2019) -
ETSI LI & RD Status (Sept. 2019) - by Gerald McQuaid and Domenico Raffaele Cione (N. III_MMXIX)
This article highlights the relevant ETSI activity on Lawful Interception (LI) and Retained Data (RD) as update to the previous article of February 2017. The 2018th and 2019th period work items are described in the following section.
 ETSI INTERFACE TO IMPLEMENT EUROPEAN INVESTIGATION ORDERS (EIOs) -
ETSI INTERFACE TO IMPLEMENT EUROPEAN INVESTIGATION ORDERS (EIOs) - by Gerald McQuaid and Domenico Raffaele Cione (N. III_MMXVIII)
The ETSI work to provide a Technical Specification (TS) to support the Directive 2014/41/EU of the European Parliament and of the Council of 3 April 2014 regarding the European Investigation Order (EIO) in criminal matters [1] had started in 2016 and was carried on during all 2017 and 2018 on all technical aspects of the new interface resulting now finalized with the publication of a first version of the Inter LEMF Handover Interface (ILHI) [4]. This specification provides LEMF’s with all implementation details to allow LI data transferring from one LEMF located in the country B (responding country where a target abroad is requested to be intercepted) to a LEMF located in the country A (requesting country where the request of interception is originated).
 ETSI LI & RD Status (Feb. 2017) -
ETSI LI & RD Status (Feb. 2017) - by Gerald McQuaid and Domenico Raffaele Cione (N. I_MMXVII)
Current ETSI activity on Lawful Interception (LI) and Retained Data (RD) is managed mainly by three main standardization committees: ETSI TC LI (the leading LI/RD group), TC CYBER and ISG NFV
 LEMF TO LEMF INTERFACE TO SUPPORT EUROPEAN INVESTIGATION ORDERS (EIOs) -
LEMF TO LEMF INTERFACE TO SUPPORT EUROPEAN INVESTIGATION ORDERS (EIOs) - by Gerald McQuaid and Domenico Raffaele Cione (N. IV_MMXVI)
Imminently, the Directive 2014/41/EU of the European Parliament and of the Council of 3 April 2014 regarding the European Investigation Order (EIO) in criminal matters [1] is expected to become part of the EU-nations’ national laws. This EU directive requires each European Member State to transpose the directive into national law by 22 May 2017 (Article 33). This EIO describes the possibilities about lawful interception (LI) of telecommunications and collection of traffic and location retained data (RD) extended to network scenarios out of a pure national network context: an EIO may be issued for the interception of telecommunications by a Member State to obtain intercepted data of a target when using a communication service in a CSP’s network located in another Member State country (ref. Article 30 of [1]).
 THE LI-INTERFACE FOR WARRANT INFORMATION -
THE LI-INTERFACE FOR WARRANT INFORMATION - by Gerald McQuaid and Domenico Raffaele Cione (N. III_MMXVI)
Traditionally the ETSI standardization work was focused on IRI and CC data details by defining, updating and maintaining related data Handover Interfaces (HI-2 and HI-3) specifications. Furthermore, ETSI had defined a dedicated Handover Interface, named HI-1, referred to be also crossing borders between countries based on corresponding international laws or agreements. HI-1 was defined as an interface between LEA and CSP to transport all kind of administrative information being used for the transmission of the request to establish or to remove the interception action from the LEA to the CSP and the acknowledgement message back to the LEA.
 Lawful interception items for VoLTE -
Lawful interception items for VoLTE - by Gerald McQuaid and Domenico Raffaele Cione (N. II_MMXVI)
VoLTE, Voice over Long Term Evolution (LTE), is a standard-based technology used to support voice calls over the LTE technology being now used by 4G wireless networks.
 ETSI AND STATUS OF LI & RD STANDARDS -
ETSI AND STATUS OF LI & RD STANDARDS - by Gerald McQuaid and Domenico Raffaele Cione (N. I_MMXVI)
This thematic section is intended to inform readers on the latest progress of standardization work items on Lawful Interception (LI) and Retained Data (RD) mainly focusing on European regional level (ETSI). The scope is to cover all relevant LI and RD aspects in terms of requirements, communication service providers architecture and network interfaces/protocols definition.
 Gerald MCQUAID - Chairman of ETSI Technical Committee for Lawful Interception and attending ETSI TC CYBER and 3GPP SA3 LI since 2004. Member of the EU Data Retention Experts Group under the auspices of the European Commission.
Gerald MCQUAID - Chairman of ETSI Technical Committee for Lawful Interception and attending ETSI TC CYBER and 3GPP SA3 LI since 2004. Member of the EU Data Retention Experts Group under the auspices of the European Commission.Other articles of Domenico Raffaele Cione
 ETSI LI & RD Status (Dec. 2022) -
ETSI LI & RD Status (Dec. 2022) - by Domenico Raffaele Cione (N. IV_MMXXII)
This document highlights the ETSI activity on Lawful Interception (LI) and Retained Data (RD) at end of 2022 as update from Q4 2021 status.
 ETSI LI & RD Status (Dec. 2021) -
ETSI LI & RD Status (Dec. 2021) - by Domenico Raffaele Cione (N. IV_MMXXI)
This document highlights the ETSI activity on Lawful Interception (LI) and Retained Data (RD) at end of 2021 as update from Q4 2020 status.
 ETSI LI & RD Status (Dec. 2020) -
ETSI LI & RD Status (Dec. 2020) - by Domenico Raffaele Cione (N. IV_MMXX)
This article highlights the ETSI activity on Lawful Interception (LI) and Retained Data (RD) as update to the previous article of September 2019.
 ETSI LI & RD Status (Sept. 2019) -
ETSI LI & RD Status (Sept. 2019) - by Gerald McQuaid and Domenico Raffaele Cione (N. III_MMXIX)
This article highlights the relevant ETSI activity on Lawful Interception (LI) and Retained Data (RD) as update to the previous article of February 2017. The 2018th and 2019th period work items are described in the following section.
 ETSI INTERFACE TO IMPLEMENT EUROPEAN INVESTIGATION ORDERS (EIOs) -
ETSI INTERFACE TO IMPLEMENT EUROPEAN INVESTIGATION ORDERS (EIOs) - by Gerald McQuaid and Domenico Raffaele Cione (N. III_MMXVIII)
The ETSI work to provide a Technical Specification (TS) to support the Directive 2014/41/EU of the European Parliament and of the Council of 3 April 2014 regarding the European Investigation Order (EIO) in criminal matters [1] had started in 2016 and was carried on during all 2017 and 2018 on all technical aspects of the new interface resulting now finalized with the publication of a first version of the Inter LEMF Handover Interface (ILHI) [4]. This specification provides LEMF’s with all implementation details to allow LI data transferring from one LEMF located in the country B (responding country where a target abroad is requested to be intercepted) to a LEMF located in the country A (requesting country where the request of interception is originated).
 ETSI LI & RD Status (Feb. 2017) -
ETSI LI & RD Status (Feb. 2017) - by Gerald McQuaid and Domenico Raffaele Cione (N. I_MMXVII)
Current ETSI activity on Lawful Interception (LI) and Retained Data (RD) is managed mainly by three main standardization committees: ETSI TC LI (the leading LI/RD group), TC CYBER and ISG NFV
 LEMF TO LEMF INTERFACE TO SUPPORT EUROPEAN INVESTIGATION ORDERS (EIOs) -
LEMF TO LEMF INTERFACE TO SUPPORT EUROPEAN INVESTIGATION ORDERS (EIOs) - by Gerald McQuaid and Domenico Raffaele Cione (N. IV_MMXVI)
Imminently, the Directive 2014/41/EU of the European Parliament and of the Council of 3 April 2014 regarding the European Investigation Order (EIO) in criminal matters [1] is expected to become part of the EU-nations’ national laws. This EU directive requires each European Member State to transpose the directive into national law by 22 May 2017 (Article 33). This EIO describes the possibilities about lawful interception (LI) of telecommunications and collection of traffic and location retained data (RD) extended to network scenarios out of a pure national network context: an EIO may be issued for the interception of telecommunications by a Member State to obtain intercepted data of a target when using a communication service in a CSP’s network located in another Member State country (ref. Article 30 of [1]).
 THE LI-INTERFACE FOR WARRANT INFORMATION -
THE LI-INTERFACE FOR WARRANT INFORMATION - by Gerald McQuaid and Domenico Raffaele Cione (N. III_MMXVI)
Traditionally the ETSI standardization work was focused on IRI and CC data details by defining, updating and maintaining related data Handover Interfaces (HI-2 and HI-3) specifications. Furthermore, ETSI had defined a dedicated Handover Interface, named HI-1, referred to be also crossing borders between countries based on corresponding international laws or agreements. HI-1 was defined as an interface between LEA and CSP to transport all kind of administrative information being used for the transmission of the request to establish or to remove the interception action from the LEA to the CSP and the acknowledgement message back to the LEA.
 Lawful interception items for VoLTE -
Lawful interception items for VoLTE - by Gerald McQuaid and Domenico Raffaele Cione (N. II_MMXVI)
VoLTE, Voice over Long Term Evolution (LTE), is a standard-based technology used to support voice calls over the LTE technology being now used by 4G wireless networks.
 ETSI AND STATUS OF LI & RD STANDARDS -
ETSI AND STATUS OF LI & RD STANDARDS - by Gerald McQuaid and Domenico Raffaele Cione (N. I_MMXVI)
This thematic section is intended to inform readers on the latest progress of standardization work items on Lawful Interception (LI) and Retained Data (RD) mainly focusing on European regional level (ETSI). The scope is to cover all relevant LI and RD aspects in terms of requirements, communication service providers architecture and network interfaces/protocols definition.
 Domenico Raffaele CIONE - Active delegate in ETSI Technical Committees for Lawful Interception (LI) and Retained Data (RD) since 2003
Domenico Raffaele CIONE - Active delegate in ETSI Technical Committees for Lawful Interception (LI) and Retained Data (RD) since 2003