by Gerald McQuaid and Domenico Raffaele Cione
VoLTE, Voice over Long Term Evolution (LTE), is a standard-based technology used to support voice calls over the LTE technology being now used by 4G wireless networks.
1. Introduction
VoLTE, Voice over Long Term Evolution (LTE), is a standard-based technology, defined by the GSMA based on 3GPP Technical Specifications, used to support voice calls over the LTE technology being now used by 4G wireless networks.
VoLTE provides subscribers with natural-sounding high-definition voice services, crisp and clear as if you were face to face. Voice calls are maintained on LTE network as for data allowing to keep 4G data sessions (e.g. browsing or file downloading) while talking. Furthermore, due to LTE connectivity bandwidth, network operators may provide conference call services with high quality, and during a VoLTE call users may share content such as photos and video clips, upgrade the audio call to a video call and establish a multi-party high quality call.
At the end of 2015 there were more than 100 million VoLTE subscriptions. The uptake is expected to accelerate in the coming years, with 2.3 billion subscriptions projected by 2021. US, Canada, Japan and South Korea, are estimated to have around 80 percent of LTE subscriptions using VoLTE by 2021. In addition, the penetration of VoLTE-capable smartphones is increasing rapidly (e.g. more than 340 VoLTE-enabled smartphone models commercialized at April 2016 supporting different regions and frequencies).
The LTE standard only supports packet switching with its all-IP network. Voice calls in GSM, UMTS and CDMA2000 are circuit switched, so with the adoption of LTE, the Network Operators have to re-engineer their voice call network. VoLTE approach is based on the IP Multimedia Subsystem (IMS) network, with specific profiles for control and media planes of voice service on LTE. GSMA specification IR.92 [1] defines a voice over IMS profile by listing a number of Evolved Universal Terrestrial Radio Access Network (E-UTRAN) , Evolved Packet Core (EPC), IMS core, and UE features that are considered essential to launch interoperable IMS based voice.
VoLTE Service Description is provided by [11] which describes the logical architecture based on the relevant components in terms of VoLTE UE, LTE, EPC, and the IMS Core Network.
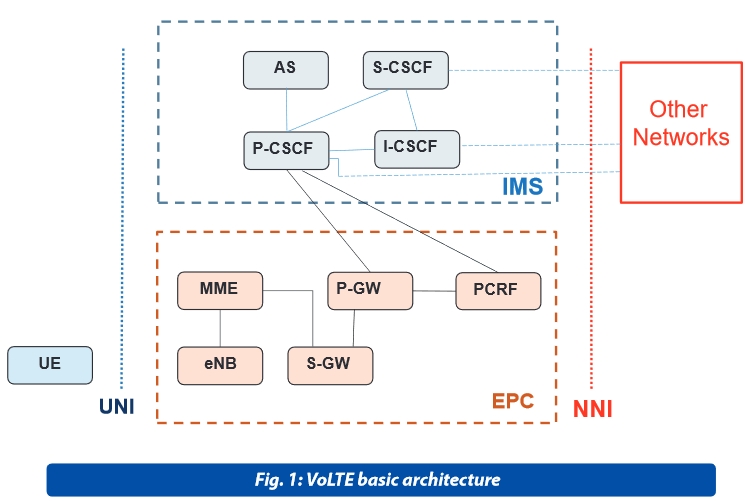
The VoLTE approach results in the voice service (control and media planes) being delivered as data flows within the LTE data bearer: there is no dependency on (or ultimately, requirement for) the legacy Circuit Switch voice network to be maintained.
ETSI refers to 3GPP specifications to define alternative specific functionalities such as CSFB (Circuit Switched Fallback, [10] see note 1) and SRVCC (Single Radio Voice Call Continuity, [9]) that allows a smooth interaction between LTE networks and GSM/WCDMA networks, in order to have coexistence and easy network upgrade.
2. Lawful Interception (LI)
Lawful Interception (LI) items for VoLTE have being addressed by ETSI primarily by means of a Study Report (SR 003 292) on items for LTE and IMS [2].
The interception of VoLTE is deployed as an interception of packetized services by using the Access Session Border Controller (ref. clause 7A of [6]) as the point of intercept, due to the available access to both the IMS signaling and the media. Deeply, the interception of Intercept Related Information (IRI) can be located in the IP Multimedia System at the level of the IMS Proxy or Serving Call Session Control Function (P-CSCF and S-CSCF). This intercept configuration is identified by Figure 1d of [6] which identifies also the administrative interface X1_1 from ADMF towards CSCF’s which provide the raw IRI to the MF/DF entities mapping them into HI2 external format to LEA.
The interception of CC for basic VoLTE call can be located in the IMS GWs or Packet Data Gateway (PDN-GW) which forwards data to the MF/DF entities formatting it into HI3 external format towards LEA.
In addition, the interception of non-IMS traffic (not covered by IMS based VoLTE interception) may be addressed by Evolved Packet Interception (EPC) as defined by [6] and [7].
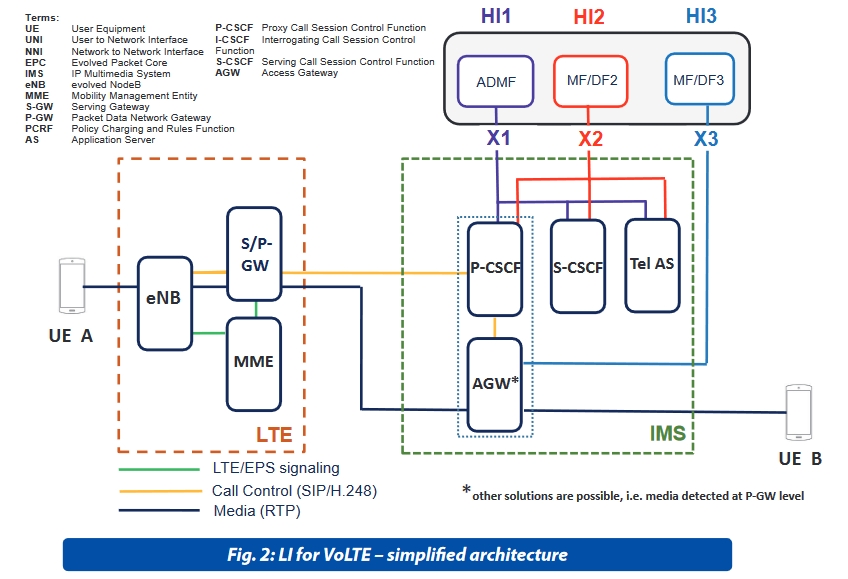
The applicable standards of VoLTE for Handover Interfaces are not uniquely defined. [2] provides indications on Pro and Con on their usage to deliver intercepted data to LEMF. ETSI refers to the 3GPP specifications [6] and [7] to address the latest development of 3GPP services with target identification based on TEL URI, SIP URI, IMSI, MSISDN, IMEI, NAI. More LEMF user friendly and resilient system related to HI3 are provided by selecting the ETSI HI TS 102 232 parts for IMS [4] in conjunction with [3] which provides also application keep alive. IMSI is not included as possible target identities. ETSI has indicated the additional HI IP delivery mechanism with the 3GPP data of [7] delivered via ETSI mobile service TS 102 232-7 [5] in conjunction of [3].
VoLTE roaming is a major standard issue for LI with reference to the two IMS voice architectures of Local Breakout (LBO) and S8 Home Routing (S8HR). 3GPP is studying LI for S8HR by means of a Technical Report [8] whose primary scope is to identify the changes to the LI architecture, function and protocols for inbound roamers in the VPLMN when S8HR is employed to allow the same level of LI functionalities as for LBO in the VPLMN for VoLTE services. ©
NOTES
Note 1 : CSFB (Circuit Switched Fallback) is VoLTE, where LTE just provides data services, and when a voice call is to be initiated or received, it will fall back to the CS domain. When using this solution, CSP’s just need to upgrade the MSC instead of deploying the IMS, and therefore, can provide services quickly. However, the disadvantage is longer call setup delay.
REFERENCES
GSMA IR.92 v7.0 “IMS Profile for Voice and SMS”
ETSI SR 003 292 LTE Frequently Asked Questions and Implementation Guidance”
ETSI TS 102 232-1 Lawful Interception (LI); Handover Interface and Service-Specific Details (SSD) for IP delivery; Part 1: Handover specification for IP delivery v3.11.1 (2016-03)
ETSI TS 102 232-5 Lawful Interception (LI); Handover Interface and Service-Specific Details (SSD) for IP delivery; Part 5: Service-specific details for IP Multimedia Services v3.5.1 (2015-10)
ETSI TS 102 232-7 Lawful Interception (LI); Handover Interface and Service-Specific Details (SSD) for IP delivery; Part 7: Service-specific details for Mobile Services v3.3.1 (2016-03)
ETSI TS 133 107 Universal Mobile Telecommunications System (UMTS); LTE; 3G security; Lawful interception architecture and functions (3GPP TS 33.107 version 13.2.0 Release 13) (2016-04)
ETSI TS 133 108 Universal Mobile Telecommunications System (UMTS); LTE; 3G security; Handover interface for Lawful Interception (LI) (3GPP TS 33.108 version 13.1.0 Release 13)
3GPP TS 33.827 v0.0.1: “Study on Providing for LI in the S8 Home Routing Architecture for VoLTE (Release 14)”
ETSI TS 123 216 V13.1.0 (2016-03) Digital cellular telecommunications system (Phase 2+) (GSM); Universal Mobile Telecommunications System (UMTS); LTE; Single Radio Voice Call Continuity (SRVCC); Stage 2 (3GPP TS 23.216 version 13.1.0 Release 13)
ETSI TS 123 272 V13.3.0 (2016-04) Digital cellular telecommunications system (Phase 2+) (GSM); Universal Mobile Telecommunications System (UMTS); LTE; Circuit Switched (CS) fallback in Evolved Packet System (EPS); Stage 2 (3GPP TS 23.272 version 13.3.0 Release 13
GSMA FCM.01 – VoLTE Service Description and Implementation Guidelines.